How to crack passwords with John the Ripper
John the Ripper (also called simply ‘John’ ) is the most well known free password cracking tool that owes its success to its user-friendly command-line interface. John has autodetect capability, which often works fine, but in some cases, it might be necessary to guess the hash type. Best practice is to make these guesses based on where these hashed passwords were obtained from.
John is already installed on Kali Linux (pentester’s favorite OS). The software can be downloaded from the website for both Linux OSs and Windows.
Password hashes
Password login is the default authentication mechanism. Passwords are normally not stored in plain text, instead, they are stored in hashed format. Whenever a user tries to log in, the entered password is hashed and compared to the stored hash value for authentication. For example, in case the system stores the passwords using the MD5 hash function, the password ‘secret’ could be hashed as follows.
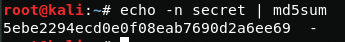
We can move this hash value 5EBE2294ECD0E0F08EAB7690D2A6EE69 into a text file and save it as passwd_file.txt.

Password cracking
Password cracking is an iterative process in which a word is selected from a wordlist as a possible password, after which the computed hash value of this selected word is compared with the password hash. This iterative process is repeated until a match is found.
We run John with the following command and specify the hash type and filename.
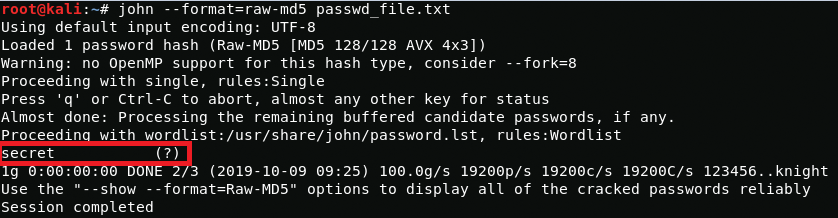
John found that the hash value stored in the file belonged to the password ‘secret’. In the screenshot above, we see in the line starting with ‘Proceeding with wordlist’ that John successfully cracked the password in Wordlist mode using John’s default wordlist file password.lst.
Preceding that, we see in the line starting with ‘Proceeding with single’ that John initially started in Single cracking mode and then proceeded to Wordlist mode after unsuccessfully crack. If that would have been unsuccessful too John would have proceeded to Incremental mode, also known as Brute-Force attack in which all possible character combinations are tried.
Modes of cracking
John supports 4 modes of password cracking:
1. Single crack mode: Tries mangling usernames obtained from the GECOS field, and tries them as possible passwords
2. Wordlist mode: Tries all words in the wordlist
3. Incremental mode (aka Brute-Force attack): Tries all possible character combination
4. External mode: Optional mode in which John may use program code to generate words.
Some other useful commands for John [— options]
#Displays all the hash types supported:
john --list=formats
Runs tests to displays the speed of cracking for various hash types:
john --test
Displays all other options available for John:
john --help



Comments
Post a Comment